 Internet Protocol version 6 (IPv6) is the next generation of the Internet Protocol that was designed to be the succeesor to the current Internet Protocol verion 4 (IPv4). It was designed by the Internet Engineering Task Force (IETF) to deal with the exhaustion of IPv4 addresses.
Internet Protocol version 6 (IPv6) is the next generation of the Internet Protocol that was designed to be the succeesor to the current Internet Protocol verion 4 (IPv4). It was designed by the Internet Engineering Task Force (IETF) to deal with the exhaustion of IPv4 addresses.
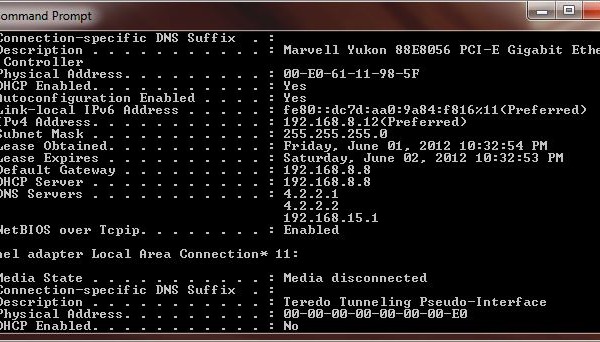
An IPv6 address has 128 bits (2128 = a number too large for human comprehension) compared to an IPv4 address which has 32 bits (about 4.3 billion unique addresses (232 = 4,294,967,296). IPv6 address is too long; it is quite difficult to handle considering the fact that we are having problem communicating IPv4 address to other people.
IPv4 has the simple form of four octets or groups of decimal numbers seperated by periods: 1.2.3.4. Now try and imaging if we keep that same format for IPv6 address; we’d have: 1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16 – it would be way to long and too difficult to remember. So our friends at the IETF decided to shorten it by breaking the IPv6 address into eight 16-bit groups and switched to Hexadecimal numbering scheme with each group separated by a colon. So a typical IPv6 address now looks like this:
2000:F53A:0000:0000:0F14:0000:0000:0053.
Even with that, it’s still way too long so they decided shorten it further by removing the leading zero’s. The aforementioned address could be represented as: 2000:F53A:0:0:F14:0:0:53. As you can see here, all the leading zero’s are removed and if any group of number has four 0’s, it’s replaced by a single 0. If that isn’t confusing enough, IETF decided that they want to shorten IPv6 address further by replacing two or more consecutive groups of 0000’s (or 0:0 for the short form) with a “::” leaving just the double colons between the groups. So the same IPv6 address above can be represented as 2000:F53A::F14:0:0:53. If you haven’t recognized it yet, we replaced “0000:0000:” with “:” right after F53A leaving “::” between F53A and F14.
Now you might question why the second consecutive groups of 0000’s didn’t get replaced; that’s because the our friends also said that you can only replace one consecutive groups of zero’s and it’s gotta be the first occurence in the event that the two groups are of equal length. The reason they do that is to guarantee that we can reproduce the fully expanded address correctly.
To demonstrate that point, let’s the the same address above and modify it a little bit: 2000:0000:0000:0000:0F14:0000:0000:0053. Now if we remove the consecutive groups of zero’s, we’d have: 2000::F14::53. Without the rule above, we can’t correctly reproduce the original address. Let’s break it down:
By looking at 2000::F14::53 we know that we have three groups of and need five more to form a complete IPv6 address. But do we put two groups of 0000’s or three groups of 0000’s at the first occurrence of the “::”? So to remove this ambiguity, the rule states that we can only have a single “::” in any IPv6 address.
To summarize, IPv6 is the next generation of IP address; it is 128 bit long and resulting a really large address space – we won’t be running out of address for quite some time to come. IPv6 address can be written in various formats with leading zero’s can be removed from each octet.
If you want to experiment with various ways to represent IPv6 format or to subnet it, check out this site.



Recent Comments